
The State of the UK’s Cyber Security
What can breaches tell us about building a more secure business for 2020?
As we head into the New Year, cyber attacks continue to be a key concern for UK organisations. Even though more businesses are boosting their cyber security spending, cyber attacks and losses due to them continue to increase.
No sector is unaffected, from charities, schools and hospitals (where cyber attacks are adding to response times and leading to an increased number of deaths) to finance, where despite massive efforts, vulnerabilities remain. New ventures, technology and partnerships bring new risks. Overall in the private sector, 61% of British firms reported a cyber incident in 2019, according to insurer Hiscox.
There are real costs to this. The regulatory penalties that can occur are the easiest to quantify. The Information Commissioner’s Office has handed out fines of £12.6m for data breaches since 2010, and with higher possible fines under GDPR, that’s likely to increase over time. Moreover, the Morrison’s data leak class action case has finally made its way to the Surpreme court in November. As lawyers explain, the decision could not only encourage other class actions for data breaches (common in the US but rare here) but, it also threatens to significantly increase potential liabilities. The breach in this case came from a disgruntled employee deliberately uploading payroll data onto a file sharing website. Up to now, the company would be considered solely as a victim in these circumstances.
The wider costs of breaches, however, often go unreported. IBM has estimated that on average a breach results in losses of £3.1million. Across the pond, a recent survey by US non-profit the National Cyber Securithttps://staysafeonline.orgy Alliance (NCSA) found that one in ten small businesses experiencing an official data breach in the previous year had shut up shop.
Not just an IT issue: phishing

So why isn’t increased spending on cyber security reducing the risk of attacks?
A big part of the problem, of course, is that cyber breaches are often more of a people issue than an IT issue. It’s not simply a case of disgruntled employees, as with Morrisons – although that’s certainly a factor. According to one recent survey three quarters of organisations have been the focus of deliberate and malicious employee action. More generally, though, majority of cyber breaches are – at some level at least – down to human error.
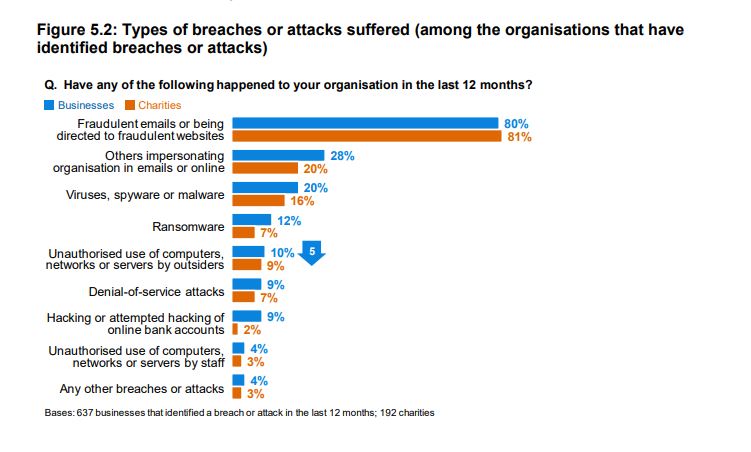
Some key areas illustrate this. The first one is phishing. We’ve looked at this extensively in the past, but there’s a reason for that: It is pervasive. Phishing was by far the most common attack identified by businesses in the government’s Cyber Security Breaches Survey published earlier this year, accounting for eight out of ten of those reporting a breach or attack in the previous year. Moreover, it’s often the gateway used to launch other attacks, such as ransomware – another big source of risk.
Where the risks are: Types of breaches or attacks suffered by organisations in the last 12 months. Source: Cyber Security Breaches Survey 2019, DCMS
As we’ve discussed before, and as National Cyber Security Centre (NCSC) guidance makes clear, the ubiquity and sophistication of some phishing attacks mean it’s not simply a case of carelessness when these attacks get through. IT-based solutions, such as IP filters and domain name protection have a role here; but people do tend to be the weak link. Anti phishing training provided by Intersys and others (and Microsoft has started to offer this as part of its Microsoft Office 365 Enterprise licenses) can make a real difference to vulnerability.
Passwords: when it comes to cyber security recycling isn’t a good thing

The second area to look at is passwords. Again, there’s a temptation to over-simplify a complex issue. It’s not simply about employees (or business owners) using “password” or “123456” – although that sadly remains a shockingly common problem.
The key issue is password re-use. Many use perfectly good passwords, but, for reasons of convenience and the limitation of memory, use the same password across accounts – personal email, social media, e‑commerce, and other websites. If any one of these experience a breach or is compromised, then all the sites where that password is used are also effectively hit. If that includes work accounts and sign ins, then a business can be in trouble, too.
In fact, this principle can be taken even further. There are a huge number of passwords that are well known to hackers and malware developers from previous attacks. The NCSC recommends checking passwords against the 100,000 breached passwords collected and released by web security expert Troy Hunt. The text file is downloadable here. It begins with the usual entries such as sequential numbers or “qwerty”, but soon progresses to less obvious efforts such as “!ab#cd$”. You can also check whether your account is one that has been compromised in a data breach – in which case, again, it’s time to change your password.
Businesses – and consumers for that matter – need to make use of these resources, because if they don’t, hackers will. Lists of known passwords are often the starting point for those looking to breach defences.
This is a people issue just as much as phishing – and they have to be at the heart of any security strategy. Of course, there are tools organisations can employ to help: password rules and automated blacklists for systems, for example, can prevent employees making bad choices by refusing to accept weak passwords. But even if a password isn’t widely known on the web, it might be possible for those with knowledge of the individual to guess – birthdays and anniversaries, for example. That’s a real risk in light of targeted social engineering fraud (such as “spear phishing”).
As ever, the answer is a combination of both IT tools and good training to keep your systems safe.
The cybersecurity threats of tomorrow – the threats of today

The final reason why people should be as much a part of your cyber security as IT solutions is that, sooner or later, the latter will fail.
It’s not just that cybersecurity will always be challenged by unknown, “zero day” vulnerabilities or next generation threats; anti malware and other IT solutions struggle even with known threats. A couple of tweaks and an existing threat is again able to bypass protections.
That’s why Shamoon was able to wreak havoc at Saudi Aramco in 2012 when it first appeared, before making a repeat appearance (in a new iteration) in other Middle Eastern oil businesses in 2016, and again last December at Italian oil and gas contractor Saipem. So many variations are possible that protecting against it is like trying to inoculate against the common cold.
That – combined with the sheer volume of malware around (two billion known variants in circulation, with up to one million created every day) and something’s bound to get through eventually.
The determining factor: cyber security incident response
But how does all this help us?
Well, first, it means that while we’re likely to see new threats and attack vectors emerge, much of what businesses face tomorrow will be similar to the threats they face today. The NCSC’s five main threats and threat vectors affecting UK organisations will be just as relevant in 2020 as they proved this year:
- Cloud services (Office 365 in particular)
- Ransomware
- Phishing
- Vulnerability scanning
- Supply chain attacks.
Businesses need to think through any connections from these threats and attack surfaces to their critical data and operations. They also need to make use of the services available to be able to make a sober evaluation of their security. We offer penetration testing and cyber gap analysis for this reason.
The second thing we can take from this is that we need to be ready for failure. That means having planned, realistic and effective strategies to respond to and mitigate successful attacks. A cyber security strategy needs to address all the key questions:
- How will incidents be identified and the extent of breach be determined?
- How can the business minimise the damage?
- What communication to regulators, customers and other stakeholders will be required?
- How can vulnerabilities be addressed and lessons learned?
- Who will be responsible for these tasks?
That last question is particularly pertinent given the continuing cyber security talent shortage. The biggest firms may have in-house resources with capacity to take on these tasks in the event of a breach that may only happen once in a year or even a few, but many others do not. Outsourced cyber security breach response services, such as that provided by Intersys, are one solution to this. This can help businesses not only respond to breaches quickly and effectively, but also identify root causes and improve the firm’s cyber security posture going forward.
Because if there’s one thing we really should take from this year, it’s that we all need to get better at learning from our mistakes.