
What if the bad guys could send malware to your employees from an email that looks like it came from inside your organisation?
This is the scenario with the latest Microsoft Teams security flaw. And it’s criminally easy for scammers to start preying on your people.
At the centre of this threat is a new piece of software called TeamsPhisher, which targets a Microsoft Teams security flaw.
Here’s the lowdown on what it is, how it works and what you need to do to stop it in its tracks.
What is TeamsPhisher?
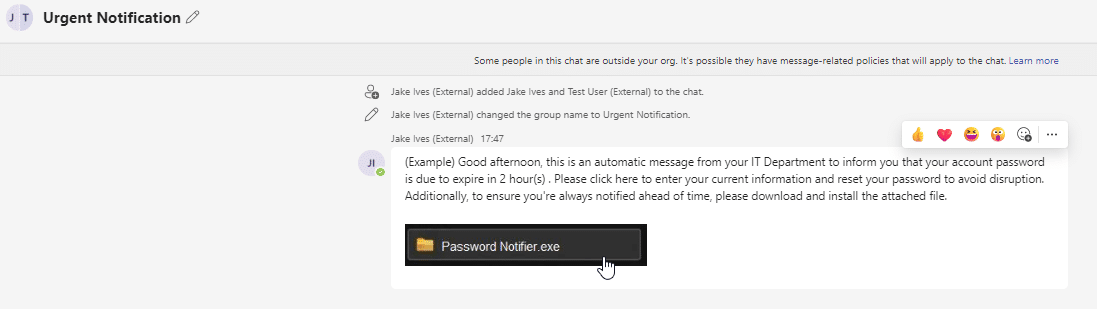
A tool that allows criminals to bypass Teams security controls and plant malware in users’ inboxes.
It creates a new thread between itself and a target and sends a message that includes a malware-laden SharePoint attachment.
It can also operate at scale, beginning with one user and then moving on to the next target and the next…
The most dangerous aspect of TeamsPhisher is that its messages look like they come internally, from employees. Obviously, this could massively increase its ability to deceive.
Bypass Teams Security? Disguise Itself as an Employee? But How?
Surprisingly easily. A Microsoft Teams security flaw allows TeamsPhisher to trick an organisation’s systems into thinking the message is coming internally. All that’s needed is a valid Teams and SharePoint license. That’s the topline.
I Can Handle the Technical Details. Bring It On.
TeamsPhisher is exploiting a well-known Microsoft Teams security flaw – an access vulnerability known as insecure direct object references (IDOR).
In this scenario, the sender of a file switches the internal and external recipient ID on a POST request (a POST request being a way to send data to a specific destination on the internet).
This enables an attacker to send the malicious email and a malware attachment.
This Sounds Bad. Who Created It? A Criminal Gang in Balaclavas?
No. The US Navy.
What?
Yes, we know. It’s a part of the story that hasn’t received much analysis in media reports.
In brief, a researcher from cyber security company JUMPSEC, Max Corbridge, highlighted the vulnerability and commented that it was ‘a potentially lucrative avenue for threat actors to deliver payloads’ because it ‘bypasses nearly all modern anti-phishing security controls.’
Enter the US Navy and its Red Team. These folk play devil’s advocate, big time, with their own organisations by submitting their systems to attack. They are essentially ‘ethical hackers.’
Their technical lead, Alex Reid, published a tool on code-hosting platform Github inspired by JUMPSEC’s findings. TeamsPhisher was born.
Seems Kind of Odd to Unleash Microsoft Teams Malware Into the Wild as an Ethical Hacking Exercise
We couldn’t agree with you more.
How Serious is This in the Big Picture?
According to Statista, there were 270 million Teams users worldwide in 2022, so the scope for TeamsPhisher to exploit organisations is significant.
Presumably, Microsoft Security Experts, as we Speak, are on a Burning Mission to Eliminate this Microsoft Teams Security Flaw and Introduce a Patch.
You’d think.
A spokesperson said they were, ‘aware of reports that security researchers developed tools seeking to bypass security in Microsoft Teams by introducing content from external sources, outside a user’s enterprise tenant.’
They also said, in a statement to security and tech news website Bleeping Computer, ‘We’re aware of this report and have determined that it relies on social engineering to be successful.’
So, No Patch?
Nothing at the time of writing. But they went on to highlight good practice, encouraging people not to click on suspicious links or unknown files.
This is good advice. However, the fact that emails from TeamsPhisher appear to be internal (and therefore safe) is problematic.
How do I Make Microsoft Teams Secure?
There are things you can do to shut out this destructive Microsoft Teams malware.
Here’s some advice from Intersys’ Senior Cyber Security Consultant, Jake Ives.
First, the ‘nuclear option.’ TeamsPhisher can only exploit organisations if Teams is configured to communicate with ‘external tenancies’ – basically, Teams users outside your organisation. If your comms are exclusively undertaken internally, you can use the Teams Admin Centre to configure Teams to shut down external comms. Job done.
What – Talk to No One Outside Our Organisation on Teams? That is Ridiculously Impractical.
Understood. Says Jake,
‘Obviously most organisations will want to take a middle ground between security and optimised business operations. I would suggest all security-conscious businesses use the features provided in the Teams Admin centre to restrict communications solely to trusted domains and organisations.
‘Also, implement the safety controls in Microsoft Defender for Office 365 such as Safe Links and Safe Attachments, which can potentially protect against this form of phishing.
‘Finally, continue to educate your people. As with much online criminal activity, Microsoft Teams malware phishing scams prey on humans – and security-aware humans are a great line of defence.’
That Sounds Promising, But I Don’t Know the Tools You Mentioned.
More from Jake on this one:
‘You should see the threat from TeamsPhisher as an opportunity to get to grips with important security functions of Teams. It is a powerful tool, but you shouldn’t leave your door wide open! If you’re not technically minded, talk to your internal or external IT provider and ask them to shore up your Teams defences.
‘Or my specialist cyber-security colleagues would be happy to help you introduce robust Teams security or train your people to manage the platform responsibly.’
Intersys is a specialist cyber-security provider that helps businesses, NGOs, schools and universities with all aspects of cyber security and Microsoft 365 support including Microsoft Teams. To find out more about how we can help you, contact us now.
For more security advice on Microsoft products, check out our Microsoft 365 security best practice guide here.