
In today’s complex threat landscape, organisations need structured approaches to manage their cyber security risks. This comprehensive guide compares the most widely adopted cyber security frameworks, helping you make an informed decision for your organisation.
Whether you’re looking to start a tendering process for a government contract, preparing for an external audit or simply keen to look at best practice standards for cyber security, you’ll find a good baseline of information here.
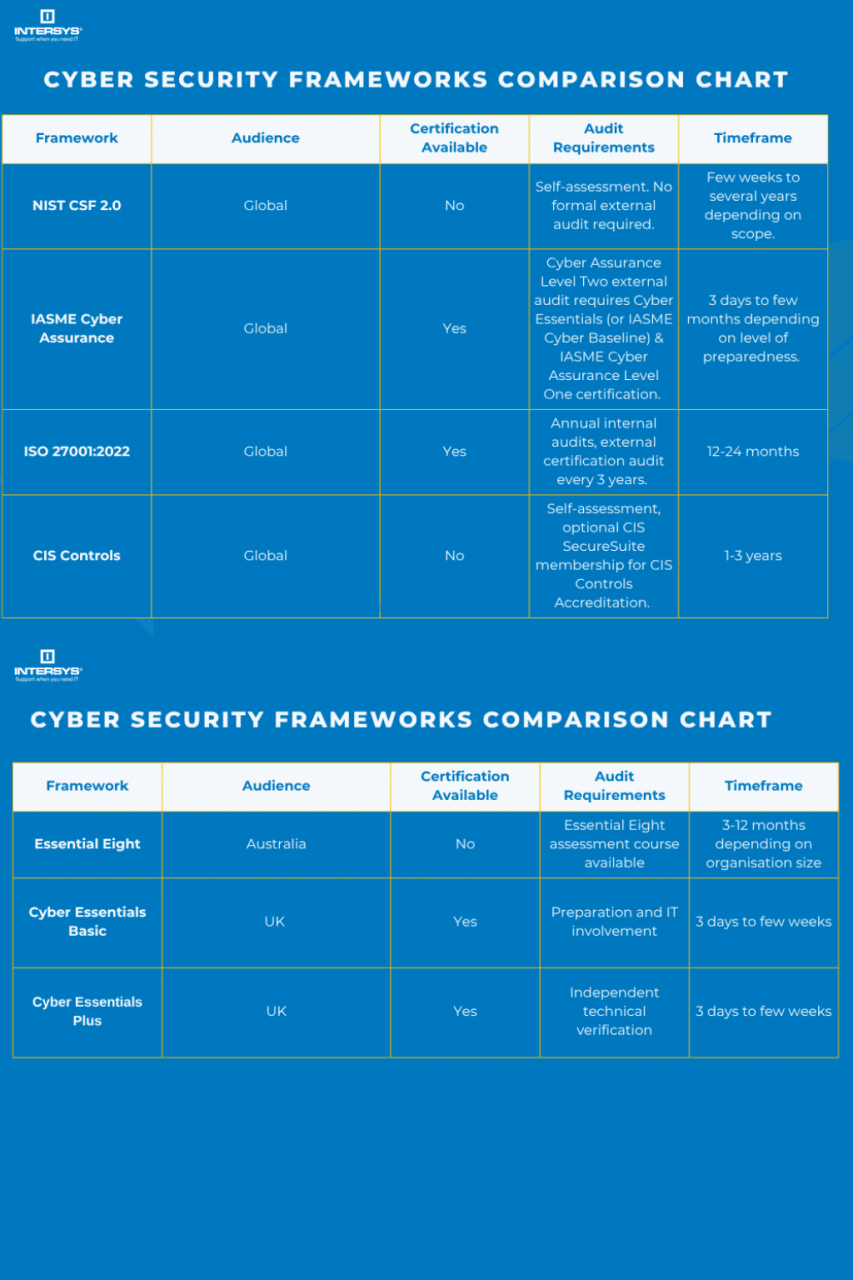
In our cyber security frameworks comparison, we focus on six leading frameworks that are the most widely used – CIS Cyber Security Framework, NIST CSF 2.0 (the most recent version), ISO/IEC 27001:2022 (the most recent version), Essential 8, Cyber Essentials Plus and IASME Cyber Assurance.
The below chart provides a quick at-a-glance view of the key elements of each framework.
Read the full blog for an in-depth analysis of each framework.
What is the CIS Cyber Security Framework?
In any cyber security frameworks comparison, the Center for Internet Security (CIS) Controls framework stands out for its practical approach. This American standard has gained international recognition and is now used globally. While it was initially developed through collaboration with US government agencies and private sector experts, organisations worldwide have adopted these controls due to their practical, risk-based approach.
The Center for Internet Security (CIS) Controls framework provides 18 prioritised safeguards organised into three implementation groups tailored to different types of organisations and their risk profile.
This framework is particularly notable for its “defense-in-depth” approach and practical implementation guidance.
The updated version of CIS Controls — v8 was created to reflect the latest developments in systems and software. It factors in developments such as the move to cloud-based computing, virtualisation, work from home and constantly changing attack strategies. You’ll find actionable ways to prevent the most common attacks, making it highly practical for organisations of all sizes.
Key features:
- 18 control categories with specific safeguards
- Implementation groups for different organisational maturity levels
- Regular updates based on emerging threats
- Strong focus on fundamental security controls (never mind the ‘nice-to-haves,’ let’s focus on the basics).
What is the NIST cyber security framework?
The National Institute of Standards and Technology (NIST) is an American government agency responsible for creating internationally competitive measurement standards for the nation’s industries.
It also develops cyber security standards, guidelines, best practices and comprehensive resources. It has been publishing the NIST Cybersecurity framework since 2014.
Cybersecurity Framework (CSF) 2.0 (last updated in February 2024) is the newest and most comprehensive version yet.
Version 2.0 is aimed at a much wider audience including all types of organisations and industry sectors regardless of their cyber security resources.
The updated framework is now organized around six (instead of the earlier five) core functions: Govern (being the latest addition), Identify, Protect, Detect, Respond, and Recover. The new governance function focuses on details of how “… the organisation’s cybersecurity risk management strategy, expectations and policy are established, communicated and monitored.” The idea being that governance actions are crucial for including cyber security into an organisation’ wider enterprise risk management strategy (ERM).
NIST CSF 2.0 introduces enhanced guidance on governance, supply chain risk management, and cyber security metrics.
Here’s a quick run through of the six core functions of CSF 2.0
- Govern: This strategic function has been added to oversee the rest of the five core functions. It looks at how cyber security is understood and catered to in the wider organisational context. Focus areas include “… the establishment of a cyber security strategy and cybersecurity supply chain risk management; roles, responsibilities and authorities; policy; and the oversight of cyber security strategy.”
- IDENTIFY: Focuses on developing organisational understanding to manage cyber security risks to systems, assets, data, and capabilities. This includes inventorying assets; understanding the business context; identifying threats, vulnerabilities and risks; establishing policies and determining risk tolerance levels to support operational resilience.
- PROTECT: Outlines appropriate safeguards to ensure delivery of critical infrastructure services. This includes implementing access control, awareness training, data security, information protection processes, maintenance, and protective technology to limit and contain the impact of potential cyber security events.
- DETECT: Defines activities to identify cyber security events in a timely manner. This includes implementing continuous monitoring capabilities, establishing anomaly detection processes, and ensuring effective detection methods to maintain awareness of unusual activity that could signal security incidents.
- RESPOND: Details appropriate actions to take when a cyber security incident is detected. This includes maintaining response planning processes, establishing communications protocols, conducting analysis, implementing mitigation procedures, and incorporating improvements based on lessons learned from incidents.
- RECOVER: Identifies appropriate activities to maintain resilience and restore capabilities or services impaired by cyber security incidents. This includes recovery planning, implementing improvements based on lessons learned and coordinating restoration activities with internal and external stakeholders.
Key features:
- Risk-based approach to security
- Flexible implementation options
- Strong emphasis on continuous improvement
- Extensive supporting documentation and resources here.
What is the ISO 27001 cyber security framework?
ISO/IEC 27001 is arguably the world’s best-known standard for information security management systems (ISMS). According to an ISO survey, over 70,000 certificates have been issued in 150 countries across a wide range of economic sectors.
The framework enables organisations to create, implement, operate, monitor, review, maintain and constantly improve their information security management system (ISMS).
In 2022, the ISO 27001 and its supplementary standard 27002 (which is part of the wider ISO 27001), were both updated to the newer ISO/IEC 27001:2022.
The update no longer refers to the framework as a “code of practice,” but rather a reference set of information security controls. ISO/IEC 27001:2022 is also much longer than the 2013 version with several controls having been reordered and updated.
The framework takes a systematic approach to managing sensitive company information, focusing on people, processes, and technology. The accompanying ISO 27002 provides detailed implementation guidance for security controls.
Key features:
- Systematic approach to risk management
- Certification capability
- Global recognition and acceptance
- Process-oriented framework
What is the Essential Eight cyber security framework?
Developed by the Australian Signals Directorate, the Essential Eight framework provides a prioritised list of mitigation strategies to help organisations protect against cyber threats. This framework is notable for its simplicity and focus on high-impact security controls.
It’s important to remember that this framework provides a minimum set of preventative measures and organisations may need to use further measures depending on their maturity model and unique environments.
What are the Essential Eight?
These are the eight mitigation strategies covered by the framework:
- Patch applications
- Patch operating systems
- Multi-factor authentication
- Restrict administrative privileges
- Application control
- Restrict Microsoft Office macros
- User application hardening
- Regular backups
Key features:
- Eight essential mitigation strategies
- Maturity model for implementation
- Regular updates based on threat intelligence
- Focus on preventing malware delivery and execution
What is the Cyber Essentials Plus cyber security framework?
Cyber Essentials Plus is a UK government-backed scheme that helps organisations protect against common cyber threats. The UK’s National Cyber Security Centre describes Cyber Essentials as the minimum standard of security that all UK organisations should aim for.
Cyber Essentials basic is a self-assessment certification where your organisation must verify that it has fundamental security controls across five key areas. Think of it as a basic cyber security health check.
- Firewalls
- Secure configurations
- User access control
- Malware protection
- Security updates
Cyber Essentials Plus includes everything in the basic certification but also adds the requirement for independent technical verification. Independent, certified assessors carry out vulnerability testing, system scans and on-site security assessments to check whether your organisation’s controls work as they should.
Key features:
- Five essential technical controls
- Independent verification process
- Annual certification
- Focus on basic cyber hygiene
What is the IASME Cyber Assurance cyber security framework?
The IASME Cyber Assurance framework is a more affordable alternative to the ISO 27001 certification aimed at smaller organisations. It is extensive and adaptable and shows an organisation’s commitment to several key cyber security, data protection and privacy measures.
There are two levels of certification offered: Level One Verified Assessment and Level Two Audited.
The audited IASME Cyber Assurance certification is widely recognised by many industries as an alternative to ISO 27001 for smaller organisations.
This risk-based cyber security framework is divided into 13 themes. Organisations need to ensure that they meet the requirements for all the themes before they can be certified against the standards.
Key features:
- Each theme implemented needs to be maintained on an ongoing basis.
- Specifically designed as an alternative to ISO 27001 for small and medium-sized organisations.
- The prerequisite for IASME Cyber Assurance is the latest Cyber Essentials certification for UK organisations and IASME Cyber Baseline for non-UK organisations.
Which cyber security framework is best for my organization?
Our Head of Security Jake Ives says,
“When clients come to me and say they are looking for a specific framework, I usually have a chat with them to discuss their specific needs to work out what is best suited for their organisation.
“It’s got to be proportionate to the size of their business. Other key factors to consider include the organisation’s location, sector, and whether they have the foundational controls already in place or not.
“For instance, they may want a NIST framework gap analysis – which is quite a mature framework – but if they’re a small company, it may not be proportionate and could work out to be quite expensive and they might be better off going for Cyber Essentials instead.
“On the other hand, if their organisation is quite mature and belongs to a highly regulated sector such as pharmaceuticals, they will need a more mature cyber security framework such as ISO 27001. Having that initial chat with your cyber security provider can help you decide which framework is best suited for your organisation’s needs.”
Best cyber security frameworks for small businesses
Small businesses typically benefit most from frameworks that emphasise fundamental controls and offer straightforward implementation guidance:
- IASME Cyber Assurance: Ideal for SMEs and a good alternative to ISO 27001.
- Cyber Essentials: Ideal for UK-based small businesses seeking basic protection.
- Essential Eight: Excellent for Australian organisations wanting a clear, prioritised approach.
- CIS Controls (Implementation Group 1): Provides foundational security controls.
Best cyber security frameworks for SMEs
Medium-sized enterprises need more comprehensive frameworks that can scale with growth:
- IASME Cyber Assurance: Ideal for SMEs and a good alternative to ISO 27001.
- CIS Controls (Implementation Group 2): Balanced approach for growing organisations.
- NIST CSF 2.0: Flexible framework that can adapt to business needs.
- ISO 27001: Particularly valuable for SMEs working with larger enterprises.
Best cyber security frameworks for enterprise organisations
Large enterprises require comprehensive frameworks that address complex security needs:
- ISO 27001: Comprehensive ISMS framework with global recognition.
- NIST CSF 2.0: Detailed guidance for complex organisations.
- CIS Controls (Implementation Group 3): Advanced controls for sophisticated security programs.
Best cyber security frameworks for highly regulated industries
Organisations in regulated sectors need frameworks that emphasise compliance and risk management:
- ISO 27001: Strong emphasis on compliance and documentation.
- NIST CSF 2.0: Detailed mapping to regulatory requirements.
- Multiple framework approach: Often beneficial to implement multiple complementary frameworks.
Key framework comparisons
NIST vs. Cyber Essentials Plus
While both frameworks aim to improve cyber security, they differ significantly in scope and depth:
- NIST CSF 2.0 provides a comprehensive approach to security risk management.
- Cyber Essentials Plus focuses on essential technical controls.
- NIST offers more flexibility but requires more resources to implement.
- Cyber Essentials Plus provides clearer pass/fail criteria.
ISO 27001 vs. NIST
These frameworks take different approaches to security:
- ISO 27001 emphasises systematic management through an ISMS.
- NIST CSF focuses on specific cyber security outcomes.
- ISO 27001 requires formal certification for compliance.
- NIST provides more flexibility in implementation approaches.
Making your decision
When selecting a cyber security framework, consider:
- Your organisation’s size and complexity
- Regulatory requirements
- Available resources and expertise
- Business objectives and risk tolerance
- Industry requirements and expectations
Remember that frameworks can be complementary, and many organisations benefit from implementing multiple frameworks in a layered approach.
Start with the framework that best matches your immediate needs and mature your security programme over time.
The most effective approach is often to begin with a simpler framework and gradually incorporate elements from more comprehensive frameworks as your organisation’s security maturity grows.
At Intersys we offer an end-to-end Cyber Essentials basic and Cyber Essentials Plus assessment service. We’ll take you through the entire process right from initial assessment, remedial action to help you achieve certification, organising the audit (in case of Cyber Essentials Plus) and the actual application process itself.