
Intersys Senior Consultant Jake Ives answers some common questions about the mysterious phenomenon of the Dark Web.
Firstly, let’s get familiar with the terminologies:
- The surface web represents just 5% of the total internet space and consists of indexable and searchable content. Let’s say you have a company website and this appears on Google or Bing, this means that your website is on the surface web.
- The deep web refers to non-indexed and non-searchable content (you won’t find it on Google) like the data you store in OneDrive, dropbox, or a website behind a layer of authentication (like a member’s area), or even your email account – The deep web represents 90% of total internet content.
- The dark web is content which is only searchable via specific software, such as the Tor network. This network can be used for both legal and illegal purposes.
Tor – The Gateway to the Dark Web

The dark web can only be accessed through a network such as Tor, an acronym for ‘The Onion Router’.
Tor was developed in the mid-1990s at the U.S Naval Research Laboratory to protect U.S intelligence communications online. This was done in response to the lack of security on the internet at the time. However, in today’s age, Tor is open source and widely used for both legitimate and non-legitimate reasons to access both the surface web and the dark web.
Applications such as Tor encrypt data sent to and from your device, hiding the contents of your internet traffic.
What does Tor Do?
- It allows you to access the dark web (i.e., onion domains), and surface web anonymously.
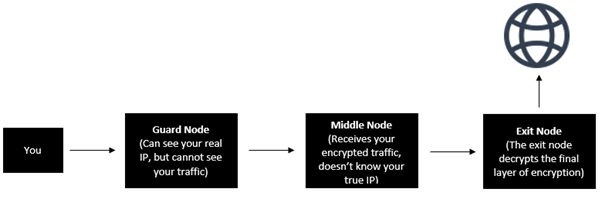
- It sends your browsing requests through three different nodes in the Tor network to lessen the chances of someone being able to trace you.
- It conceals your real IP address from the website you’re accessing.
Is Using Tor Illegal?
It depends on your location and what you use it for. Some authoritarian countries like China, Iran, Russia, Saudi Arabia and Venezuela have either banned or are in the process of banning Tor. But in most of the rest of the world, including the UK, Tor is legal.
Tor can be used for many legitimate reasons including security, legal and human rights research; whistleblowing, democracy activism (it was used by organisers of the Arab Spring to avoid state censorship), or by law abiding citizens who have legitimate concerns about their online privacy.
However, it also has a reputation as a tool for criminals who use it for a range of unlawful activities from drug trafficking and money laundering to hosting explicit and abusive content. This means that simply connecting to the Tor network alone might be enough to raise eyebrows and draw unwanted attention. Remember that your internet service provider and government agencies can still see that you’re using Tor.
How does Tor Keep My Browsing Private?
When you use an application such as Tor, you send your traffic through three random servers (also known as relays) in the Tor network. The last relay in the circuit (the “exit relay”) then sends the traffic out onto the public Internet. Nodes (servers) and exit nodes are operated by random individuals as opposed to regular servers that are run by legitimate communities or companies.
Are There Any Legitimate Uses for the Dark Web?
There are some legitimate uses for the dark web. Tor is typically used by human rights and democracy activists and is a valuable tool in avoiding surveillance. However, it’s always worth noting that:
- When you connect to the dark web (via an application such as Tor), the entry node can see your IP address and your ISP knows that you’re using it. So, if you’re trying to use the network for legitimate purposes while trying to avoid surveillance, you should use a VPN to connect to the Tor network, especially if you’re in a country which blocks access to the Tor network.
- Even though traffic is effectively scrambled once you’re connected to the Tor network (since data is sent to three different random servers), at the most basic level, you should always connect to resources via HTTPS. Accessing the Internet over non-encrypted protocols such as HTTP, or email via SMTP with no TLS could land you in a position whereby the ‘Exit’ node can intercept your communication.
What Specific Actions on the Dark Web could put my Data and Systems at Risk?
- A good example would be accessing a website which doesn’t start with HTTPS:// and inputting user details into a member’s area. A site that lacks the HTTPS:// protocol is not secure and there’s a good chance that your details may be leaked.
- Sending email using SMTP without TLS enabled (a security protocol that encrypts email for privacy). It means your email will be unencrypted and thereby available to read in plain text, by anyone who intercepts your message.
Tor vs VPN
So, how do Tor and a VPN compare? Well with Tor, due to the absence of a direct connection between the client and online service, it is significantly slower to use than a VPN.
When you use Tor, your traffic goes through three nodes in the Tor network. Consequently, it takes significantly longer to load a resource in your web browser, especially if those three nodes are spread randomly across the world. Think about it, let’s say you browse to bing.com via Tor, you are sending your request to access that site via three random computers. This has a huge impact on latency or how fast the website loads.
When you use a VPN, you’re typically connecting to a single server and then ‘traversing’ all of your internet activity via that server. Hence website loading time is faster than via Tor.
Some other differences include:
- Tor is free, a VPN usually isn’t
- Tor provides access to the dark web, a VPN itself doesn’t
- Both solutions conceal your real ISP assigned IP address
- Tor is decentralised, a VPN is not. A VPN reroutes your data through a single, privately-owned server of your choice, while the Tor network works by passing your request through a random, decentralised network of nodes (servers) to transfer data.
- Because Tor is decentralised, you have no idea who is operating the nodes or where your traffic is being sent – can you trust it?
- Tor is not widely compatible with the applications you use, unlike a VPN
- There is no customer support with Tor
- Tor is not great for streaming
What are the Risks of Using Tor?
You need to know what you’re doing and understand the risks if you’re going to consider using Tor. Can you really trust content on servers that are operated by random individuals anywhere in the world? Typical risks include malware infections, exposure to hackers and illegal content and activities.
Are There Safer Ways for me to Remain Anonymous while Browsing?
The best option is to use a paid VPN from a legitimate provider such as NordVPN, or another service which doesn’t collect data about their users. It’s a good solution to protect your identity when browsing the Internet in coffee shops, airports or on public WiFi. Nord’s website states that independent auditors have confirmed their no-log VPN policy. The general rule of thumb is to avoid free VPN providers, and those that do not have a good reputation.
How do I Know if my Data is on the Dark Web?
Our advanced tools scan the dark web looking for compromised accounts.
We can offer a free check to find out if accounts and passwords on your domain are compromised.
Jake’s Tips for Home Users on Staying Safe Online Without the Need for Tor:
- Avoid accessing content via non-secure websites that begin with HTTP instead of HTTPS
- Use DNS over TLS to encrypt DNS Queries (Services such as Quad 9, CloudFlare are great)
- Use a reputable VPN provider that doesn’t collect logs when browsing the internet in coffee shops, or while connected to public locations
- Always change your default router password, and don’t reveal it to your neighbours
- Ask your ISP for a new router every other year
- Disable UPNP and WPS on your home router
- Change your router password regularly
- Use anti-virus, and ensure your software firewall is enabled
- Keep your operating system up-to-date
- Place IoT devices on a guest network, or segregated network if your router allows this, and buy devices from reputable companies.
- Keep software up-to-date
- Only install browser add-ins from reputable sources
- Never open your router up to the outside world for remote management
Jake’s Security Tips for Businesses:
- Purchase a firewall from a reputable vendor such as WatchGuard
- Control outbound traffic by defining a specific set of policies
- Ensure vulnerable ports such as SMB, RDP are not directly exposed to the Internet – If it’s necessary to keep these ports open, expose them behind a VPN or authentication gateway.
- Ensure Firewalls and networking appliances are kept up-to-date
- Use an MDM solution such as Intune to centrally manage the roll out of software within the organisation and keep it up-to-date.
- Always change the default passwords that ship with new equipment
- Employ a good layer of gateway email security (i.e Microsoft Defender for Office 365, or Intersys Email Security)
- Segregate guest traffic by implementing VLANs
- Use open source intelligence tools such as Shodan to monitor your businesses exposure to the Internet, or sign up to an SOC Service.
- Enable HTTP & HTTPS proxies and web content filtering
- Permit DNS queries to authorised services only
Jake’s Verdict
Using Tor to get on the dark web can be an important privacy tool for human rights activists, journalists and whistle-blowers. However, it’s also a marketplace for illicit activities. The average user who is concerned about their online privacy is better off following basic privacy precautions rather than dabbling in Tor.