
Quick Quiz. Which of these things can a QR code do?
- Open a URL
- Download an application
- Add a personal contact
- Compose an email
- Connect to Wifi
- Send and receive payment
- Share a location
Trick question.
It can actually do them all.
Since the pandemic, QR (short for ‘quick response) codes have become increasingly common. Yet most of us seem to have little idea of their capabilities. The QRurb Your Enthusiasm 2021 report by cyber security firm Ivanti revealed only 47% of people knew they could open a URL and 37% that they could download an application.
And you know what happens when we use tech we don’t fully understand, right? Enter the folk in the sinister hoodies…
Cyber criminals are increasingly using QR codes as part of… wait for it… ‘quishing’ campaigns. This ignoble monicker now joins phishing, smishing and vishing in an unholy quartet of ‘ishing’ scams.
In this post, we’ll look at what qishing is and help you answer the question: ‘Is that QR code malicious? And could opening it bring a world of pain on our organisation?’
I Kind of Know But… What Exactly is a QR Code?
A QR code is a two-dimensional barcode that holds data in a black and white grid pattern. It can store website URLs, network details, email addresses, Wi-Fi passwords and more. QR codes can be found in emails and print publications, and even posters and stickers on the street. Users scan a QR code with their phone to access data – for instance, to visit the website contained in the code.
Why are We Talking About QR Codes Right Now?
QR codes were deployed widely in the pandemic as a way to minimise human contact in restaurants, bars and shops. They’re now pretty mainstream, which makes exploiting them an opportunity for criminals.
What is Quishing? And How are QR Codes Used Exactly?
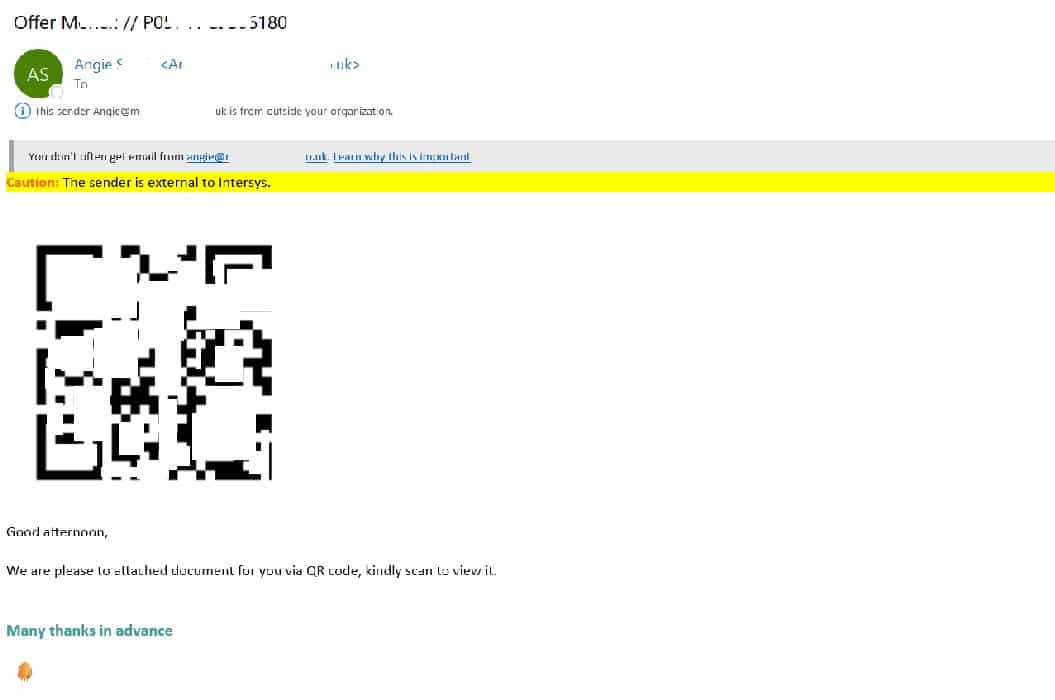
Qishing is the increasingly popular term used to describe a phishing scam that uses a malicious QR code to gain access to its victim’s logins. Like phishing, qishing attacks typically come via a message that mimics an official channel, for instance a legitimate company email.
A QR code is embedded in the email as an image. It will contain a link to a malicious URL containing malware, or a URL leading users to a phishing site that prompts users to release sensitive login data.
These attacks are commonly disguised as multifactor identification prompts from well-known businesses such as Microsoft or DocuSign.
The attacker tries to trick a user into thinking a session has expired and prompts them to sign in again, using the QR code embedded in the email. The link sends users to a fake website that harvests their login data.
What About Those QR Codes I See in the Street?
Be careful. Covering up a real QR code with a malicious one – using a QR sticker for instance – is a very common form of qishing scam. As per the email example above, it may mimic a company website, take you to a login page and steal your credentials.
Why is This Form of Scam Considered So Deadly?
Several reasons:
It’s hard to spot a spoof QR code
QR codes are not readable by humans and it’s incredibly difficult to spot a malicious one. (Compare that to the dodgy spot-them-a-mile-off website URLs you often receive in scams.)
QR codes often pass email security filters
This is because they are images – often PNG or PDF attachments – and these can bypass attempts to scan dodgy content.
QR codes are accessed by mobile, a particularly soft target
Three reasons why mobiles are vulnerable:
1. They are frequently used outside of the workplace, which means they don’t benefit from the safeguards of a business setting.
2. They are typically less secure than laptops or computers.
3. People use mobiles when they are distracted and less than vigilant.
Who is Falling Victim to Qishing Scams?
Email security threat expert Cofense has observed a dramatic increase in qishing since May 2023. Energy, manufacturing, insurance, technology and financial services have been targeted in particular, but of course it can happen to anyone and you should be vigilant.
Is That QR Code Malicious? Look Out for This Type of Scam
The Cofense data singles out qishing campaigns for Microsoft user credentials in particular. The campaigns spoofed Microsoft security notifications, luring people to fake websites via the QR code to apparently update account security, including 2FA and MFA settings.
In most cases Bing redirect URLs were used. The attackers used a URL shortener provided by a legitimate provider or sometimes placed a Captcha code in front of the malicious website so that email filtering services were unable to index the page to provide a verdict around whether or not it was malicious.
What Intersys Says About The Qishing Security Threat
Mark Kirby, Director of Professional Services at Intersys, says,
“These emails are doing the rounds and I’ve seen around 15 of them now in my work with clients. It’s concerning and Microsoft users are frustrated that they don’t block these malicious QR codes as part of their filtering process. Hopefully, this increased attention and concern drives Microsoft and other email security vendors to incorporate an AI element into their products to detect and block them.”
What Should I do to Help Prevent a Qishing Attack?
Jake Ives, Senior Consultant in Intersys’ Professional Services Division, says,
“If you receive an email from anyone containing an image of a QR code, please do not scan it. If you have scanned the QR code, please inform your IT team. You (or your team) should also reset the password, sign out sessions, and check sign in logs on the account as well as application consents.”
This is an evolving threat, so a final word from Jake about showing proper caution. “Don’t try to interact with the QR code internally either. This is a fairly new attack strategy and it’s not fully clear as to how it is currently being utilised. In most cases, the threat actor will point you to a real Microsoft sign in page which is served through a malicious proxy site and allows the actor to intercept the traffic and steal session tokens, making it resistant to Multi-Factor Authentication.”
Intersys is a specialist cyber-security provider that helps businesses, NGOs, schools and universities with all aspects of cyber security services as well as a fully managed SOC-as-a-service. To find out more about how we can help you, contact us now.