
A while back we posted about the man-in-the-middle attack (or MitM attack) problem called EvilProxy.
Recap: a man-in-the-middle attack is where a criminal places their own bogus website between a user and an application, often to harvest login details. The real headline about these attacks is that they could breach what many thought to be unassailable multi factor authentication, or MFA.
EvilProxy is an off-the-shelf MiTM attack software that could be quickly and easily deployed. So quickly and easily, that attacks rocketed.
And they continue to do so. Our Head of Security at Intersys, Jake Ives, is hearing alarming reports about man-in-the-middle attacks using Microsoft Dynamic 365 Customer Voice and wants Intersys blog readers to know about it and stay protected.
Here’s a Q&A with the facts.
What is Microsoft Dynamics 365 Customer Voice?
Microsoft Dynamics 365 Customer Voice is a feedback tool that uses personalised surveys across many channels to help organisations track customers’ perceptions of services and products.
Users across the globe range from healthcare providers and non-profits to educational institutions and businesses. In other words, the potential for you to come into contact with Customer Voice is considerable.
How does this relate to the man-in-the-middle attack problem?
Threat actors are actively exploiting Microsoft Dynamics 365 Customer Voice to redirect users to a MitM attack phishing page. For instance, a survey will contain a link directing them to the insecure destination.
But how can they do this on a Microsoft platform?
Criminals have found a bug in the Microsoft Customer Voice service, which they are exploiting to generate links that look genuine. This issue is compounded by the fact that most organisations have allowlisted or whitelisted (allowed files to execute from) the Microsoft domain.
How does the scam work exactly?
In a man-in-the-middle attack, users who click a bogus link in Customer Voice are redirected to a third-party site that sits behind the CloudFlare network. (Like Microsoft, the original source of the attack, CloudFlare is also a trusted service.)
The third-party site hosts a proxy website – the ‘man-in-the-middle’ – that renders the REAL Microsoft 365 sign-in page.
If you sign into the website using your valid credentials and multi-factor identification (MFA), your session token is stolen and used by the threat actor.
Your account is now compromised.
How do I stick it to the man (in the middle)?
There’s two ways to fight back against this threat.
Do this if you believe you’ve been compromised
Report a man-in-the-middle attack and the source, then sign out from your accounts everywhere. This is possible in one swift action, but if you don’t know how to do it, ask your IT department (or your partner such as Intersys).
You should then change your password.
Our Head of Security Jake adds,
‘Some of these attacks are very sophisticated and conniving. Therefore, you should never feel silly. The sooner you report it the better. If you flag up the issue in good time, the likelihood is that nothing will come of it.’
Do this to prevent attacks
- Get robust email security solutions: Ensure your preferred solution includes the ability to scan links present in emails and the content in the page.
- Configure Microsoft Authenticator correctly: Deploy the Microsoft Authenticator application to its full potential. Microsoft Authenticator allows you to set up MFA. You can augment this by also introducing number matching, a security measure introduced to Microsoft Authenticator in 2023. This mandates a user must do more than merely ‘okay’ a sign-in on their authentication device by tapping – they must also input a number displayed on the log-in screen into the app.
How to set up multi-factor authentication (MFA) in Microsoft Authenticator
Finally, by allowing number matching, you can also include the location of the sign-in, which could alert you of suspicious activity.
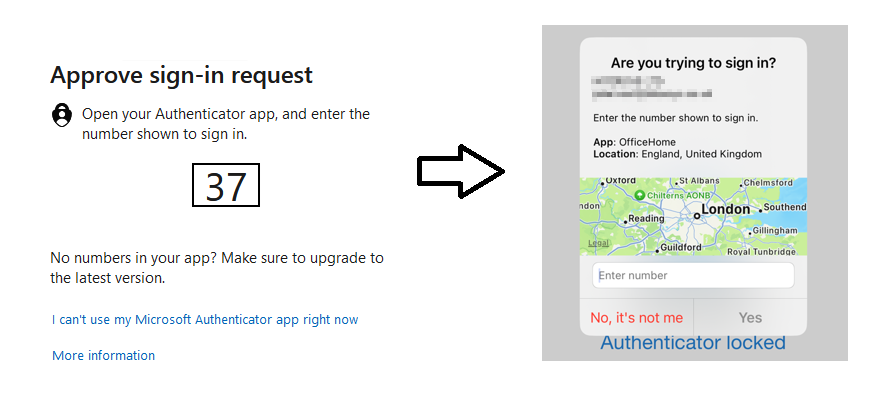
While these measures are not foolproof against a man-in-the-middle attack, they will strengthen your overall defences. For instance, in the case of the location display, it is possible for criminals to make a remote location appear to be in the country your business operates. However, only the more sophisticated hackers will be able to and you’ll detect most fraudsters.
3. Educate your team: We bang on about this again and again, because user education is at the heart of good cyber security. 88% of attacks occur through user error, so you should dedicate resources to creating a cyber-crime savvy workforce.
Ensure your people get security awareness training about phishing attacks, including fake login pages. While criminals are constantly upping their game, telltale giveaways, such as a suspicious-looking URL can help your people stick it to the man (in the middle). See the next point.
4. Learn to recognise telltale signs of an attack: stay alert for indicators like misspellings, formatting issues and do check the address bar for dodgy-looking URLS. Gone are the days where looking at the padlock in your browser is all you need to do to check if a site is credible.
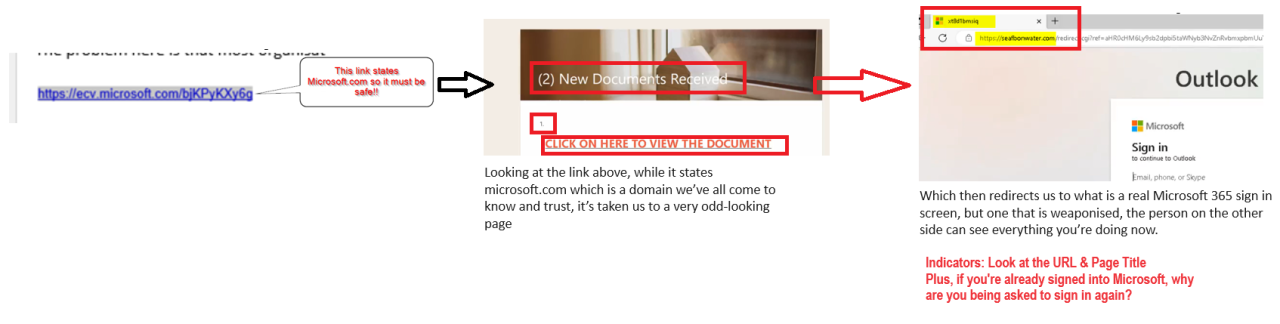
In the below example, a URL that at first glance looks like it could be Microsoft’s, turns out to be a phishing page. Always look at the URL and page title. Also, if you’re already signed into Microsoft, why are you being asked to sign in again?
5. Make use of a security operations centre as a service (SOCaaS): This is the highest level of security available and your best defence against a man-in-the-middle attack. Reputable providers will deploy sophisticated alerts around suspicious activity and ‘impossible travel’, where someone’s account is accessed from two different locations in an unfeasibly short period of time.
Is it just the chaps launching these attacks, then?
Man in the middle is kind of a dated name, isn’t it? Some people call them ‘Meddler in the Middle’ or ‘Adversary in the Middle’ attacks to avoid the male-centric title. But a man-in-the-middle attack is the best-known name for this activity and we’ve stuck to that for clarity and reach. We want as many people to see this post as possible.
No doubt, there are many ‘woman in the middle’ incidents too.
Is this attack on Microsoft platforms limited to Microsoft Dynamics 365 Customer Voice?
No. We’ve highlighted attacks on Customer Voice because they’re particularly prevalent at the time of writing this post (January 2024). However, there are other examples of criminals weaponising Microsoft’s own services. As per the Customer Voice example, they deceive and redirect you to fake websites which display the real Microsoft 365 sign-in page.
Says Jake,
‘If you’ve received a DocuSign request, iTunes voucher or anything out of the blue you’re not expecting, ignore it and report it – irrespective of whether the usual suspicious indications are present.’
Intersys is a specialist cyber-security provider offering a fully managed SOC-as-a-service to highly regulated industries such as pharmaceuticals, life sciences, business reinsurance, schools and many more sectors. We also offer fully managed IT support. To find out more about how we can help you, contact us now.