A recent article in Forbes looked at cyber security trends for 2024.
An escalation in ransomware attacks and AI-based social engineering (basically chatbots helping to relieve people of their money and data) featured prominently.
But then, so too did the rise of AI in cyber security. More and more, we’ll see AI’s ability to zoom in on even the smallest anomalies and deviations in behaviour to raise the alarm and shut out criminals.
In other words, the cyber security arms race continues. While criminals are upping their game with AI, we must all adopt new and better technologies to protect our systems.
Here’s the latest breaches, security warnings and tips to help you stay safe.
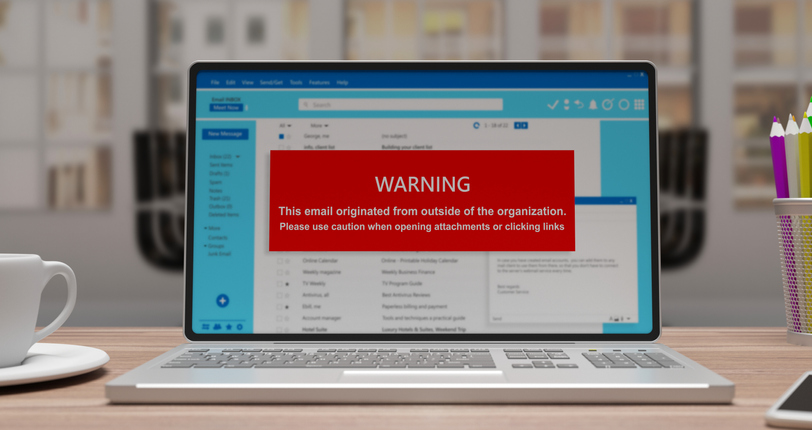
When should you be sceptical about emails? Answer: always
Many businesses struggle to tell genuine email inquiries from fraudulent ones.
For instance, is that request for a quote genuine? Or was it sent from a bogus email account used to harvest your details for an upcoming scam? (True story.)
And what about the order that was delivered but never paid for? Turns out it was placed from a compromised account. (Another true story.)
Our advice is to ALWAYS stay sceptical. Watch out for telltale signs such as unrecognisable email addresses, generic emails that don’t mention you by name and any email that is marked as external by your email service.
It’s important for everyone in the team – whether technical, finance, operations or business development – to keep a cold, steely eye on their inboxes and report anything suspicious.
Stick it to the man
Jake Ives, Our Head of Security, has warned of a new type of sophisticated ‘man-in-the-middle’ phishing attack that has been doing the rounds in business inboxes this month. Hackers are exploiting Microsoft’s own services to deceive and redirect users to fake websites, to steal their login information.
A quick excerpt from our latest blog post:
A man-in-the-middle attack is where a criminal places their own bogus website between a user and an application, often to harvest login details. The real headline about these attacks is that they could breach what many thought to be unassailable multi-factor authentication, or MFA.
According to Jake, if you’ve been stung by a man-in-the-middle attack you are essentially that person who walks into an internet café, signs into Microsoft with your company account details, passes MFA… and then walks out leaving the browser open. Meanwhile, the suspicious-looking bloke who was standing over your shoulder sits down in your vacant seat and gets free access to your account.
Chilling.
Stick it to the man (in the middle). Read our blog post on preventing this nasty attack.
Now that’s what I call data breaches volume 1
Do you like compilations? You won’t like this one.
Experts at SecurityDiscovery.com and Cybernews have revealed the mother of all data breach compilations that has exposed 26 billion records from some of the biggest digital brands in the world including X, LinkedIn, Canva, Adobe and Telegram. Government data from countries such as the US, Germany, Brazil and Turkey are also part of the list.
This is essentially a library database of previous leaks, breaches and privately sold databases and doesn’t contain data from any new breaches. It’s believed that the anonymous owner could be a ‘malicious state actor, data broker or a service that works with large amounts of data.’
Experts are particularly concerned that ‘threat actors could leverage the aggregated data for a wide range of attacks, including identity theft, sophisticated phishing schemes, targeted cyberattacks, and unauthorized access to personal and sensitive accounts.’
Spear phishing attacks, spam emails and hacks are all on the cards, particularly for anyone who frequently reuses their usernames and passwords. There’s never been a better time to sign up for a password manager and change all your passwords.
The Russians are coming...for Microsoft
Cyber security is a constantly evolving challenge and no one gets it right all the time – even senior cyber security folk at the tech giants.
This month, Microsoft confirmed that Russian hackers had managed to steal emails and attachments belonging to some of their senior executives in the company’s cyber security and legal departments.
Microsoft has identified the attackers to be a Russian advanced persistent threat (APT) group known as Midnight Blizzard.
It is believed that hackers used a password spray attack (attempting the same password on multiple accounts, before trying the next password) to get into a tenant account. This then gave them access to a ‘very small percentage of Microsoft corporate email accounts’.
Microsoft has shared guidance on the importance of auditing current privilege levels for all identities (user and service) and particularly scrutinising those with high privileges in Exchange Online.
This just in...Chinese hackers breached VMware TWO YEARS AGO
Zero Day flaws are vulnerabilities known to hackers, but completely unknown to the victim. This can lead to a long-term and devastating espionage campaign.
In the latest example, a group of Chinese hackers is believed to have exploited a security vulnerability in the VMware vCenter Server since late 2021.
The flaw is being tracked as CVE-2023 – 34048, an out-of-bounds write that can be used by threat actors to run malicious code on the victim’s computers or networks. Details of patches and updates are available in this advisory.
Shop local, steal local
If a fresh wave of cyber attacks in the New Year is anything to go by, hackers are keeping it local – and regional authorities must beware.
The Liverpool City Region Combined Authority confirmed that one of its third-party suppliers had been hit by cyber attacks and that this had affected services provided on the Merseytravel and Mersey Ferries websites.
Meanwhile, three different councils in Kent are currently investigating potential security incidents that have disrupted their online services.
Local councils appear to be soft targets for hackers. In the notorious case of Redcar and Cleveland council, a 2020 data breach ended up costing the taxpayer more than £7m.